Safeguarding Passwords: A Comprehensive Guide to Bcrypt in Backend Development
Introduction:
In the ever-evolving landscape of backend development, security remains a paramount concern, especially when it comes to user authentication and password protection. Bcrypt, a battle-tested and widely acclaimed library, stands as a fortress against unauthorized access. This comprehensive guide aims to provide an in-depth exploration of Bcrypt, unraveling its fundamentals, implementation, best practices, and real-world applications in the realm of backend security.
Understanding Bcrypt:
Introduction to Bcrypt:
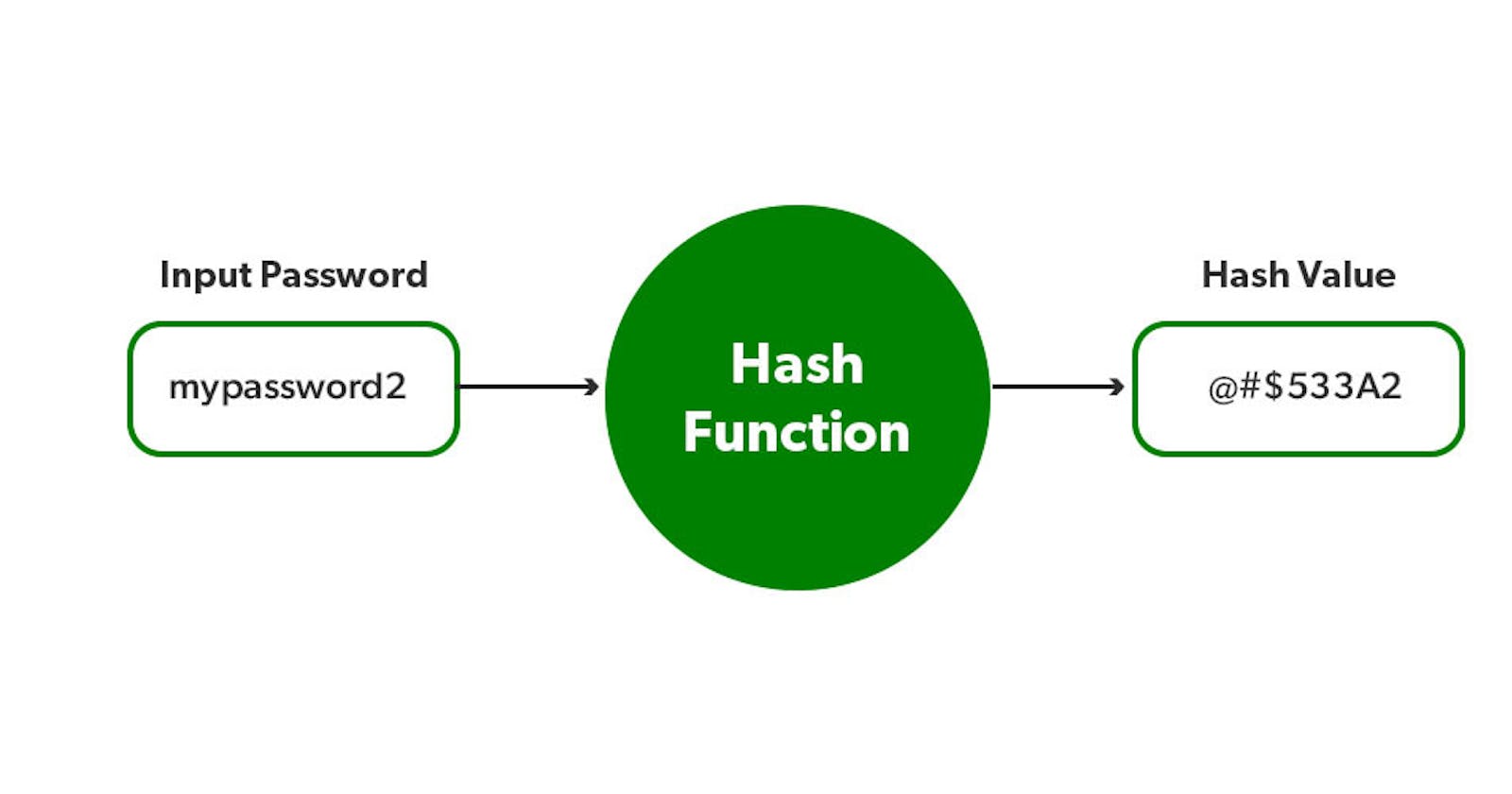
- Bcrypt is a cryptographic hashing function designed to secure passwords. It employs a unique key derivation function known for its adaptive nature, making it resistant to brute-force attacks.
Why Bcrypt?
- Bcrypt addresses the shortcomings of traditional hashing algorithms by introducing features like salting and adaptive hashing, significantly enhancing password security.
Getting Started with Bcrypt:
Installation:
- Step-by-step instructions on installing Bcrypt in a Node.js project using npm or yarn.
Basic Usage:
- Demonstrating the basic implementation of Bcrypt for hashing and verifying passwords, ensuring secure storage and authentication processes.
Salting:
- Understanding the concept of salting in Bcrypt, a crucial step in preventing rainbow table attacks and adding an additional layer of security.
Bcrypt Hashing Process:
Hashing Algorithm Overview:
- A detailed explanation of the hashing algorithm employed by Bcrypt, including its key derivation function and how it contributes to password security.
Cost Factor:
- Exploring the concept of the cost factor in Bcrypt, which determines the computational intensity of the hashing process and can be adjusted to balance security and performance.
Salting Strategies:
Dynamic Salting:
- Implementing dynamic salting strategies in Bcrypt to generate unique salts for each password, thwarting precomputed attacks and increasing resilience against brute force attempts.
Peppering:
- Exploring the concept of peppering in Bcrypt, an additional layer of security involving a secret value combined with the salt to further fortify password protection.
Best Practices with Bcrypt:
Hashing User Passwords:
- Best practices for hashing user passwords with Bcrypt during the registration process, ensuring secure storage in databases.
Password Verification:
- Guidelines for verifying user passwords during the login process, implementing Bcrypt's verification methods for a secure and seamless authentication experience.
Updating Hashed Passwords:
- Strategies for securely updating hashed passwords, considering scenarios like password resets or user-initiated changes.
Security Considerations:
Brute-Force Resistance:
- Understanding how Bcrypt's adaptive nature and cost factor contribute to its resistance against brute-force attacks, enhancing the overall security posture.
Rainbow Table Defenses:
- Exploring how salting and dynamic salting strategies in Bcrypt serve as effective defenses against rainbow table attacks, a common vulnerability in traditional hashing algorithms.
Integration with User Authentication Systems:
Integrating Bcrypt with User Authentication:
- Seamlessly integrating Bcrypt into user authentication systems, ensuring that hashed passwords are securely stored and verified during login processes.
Two-Factor Authentication:
- Complementing Bcrypt with two-factor authentication strategies for an added layer of security in user authentication workflows.
Real-world Applications:
User Authentication in Web Applications:
- Implementing Bcrypt for user authentication in web applications, safeguarding user accounts from unauthorized access and data breaches.
Securing API Endpoints:
- Extending Bcrypt's security benefits to API authentication, fortifying backend systems against malicious actors attempting unauthorized access.
Logging and Monitoring:
Logging Password-Related Activities:
- Implementing effective logging mechanisms for password-related activities, aiding in auditing, troubleshooting, and monitoring potential security threats.
Monitoring with Analytics:
- Utilizing analytics tools to monitor authentication patterns, tracking failed login attempts, and identifying potential security incidents.
Conclusion:
Bcrypt stands as a stalwart guardian in the realm of backend security, fortifying user passwords against a myriad of threats. This comprehensive guide has explored Bcrypt from its installation to advanced security strategies, with real-world applications and considerations for integrating it into user authentication systems. As you integrate Bcrypt into your backend applications, may your security measures be robust, adaptive, and resilient against the evolving landscape of cybersecurity threats.